
Splunk Part 02: MITRE ATT&CK and Behavioral Mapping
Understanding the MITRE ATT&CK framework and how security events in Splunk align with adversary behavior.
Practical cybersecurity and technical deep dives.

Understanding the MITRE ATT&CK framework and how security events in Splunk align with adversary behavior.

How to install Splunk Enterprise & perform basic searches using SPL for security monitoring.

A detailed walkthrough of Snort 3 basic configuration, HOME_NET, rule loading, and validation.

How to install Snort on Kali Linux using both repository and source-based methods.

An in-depth, defensive guide to Cloudflare with practical steps, configuration tips, and verification suggestions.

How mentorship and collaboration led to the creation of CyberSecHub, a free cybersecurity awareness site for students and communities. Lessons learned, tech stack, and impact.
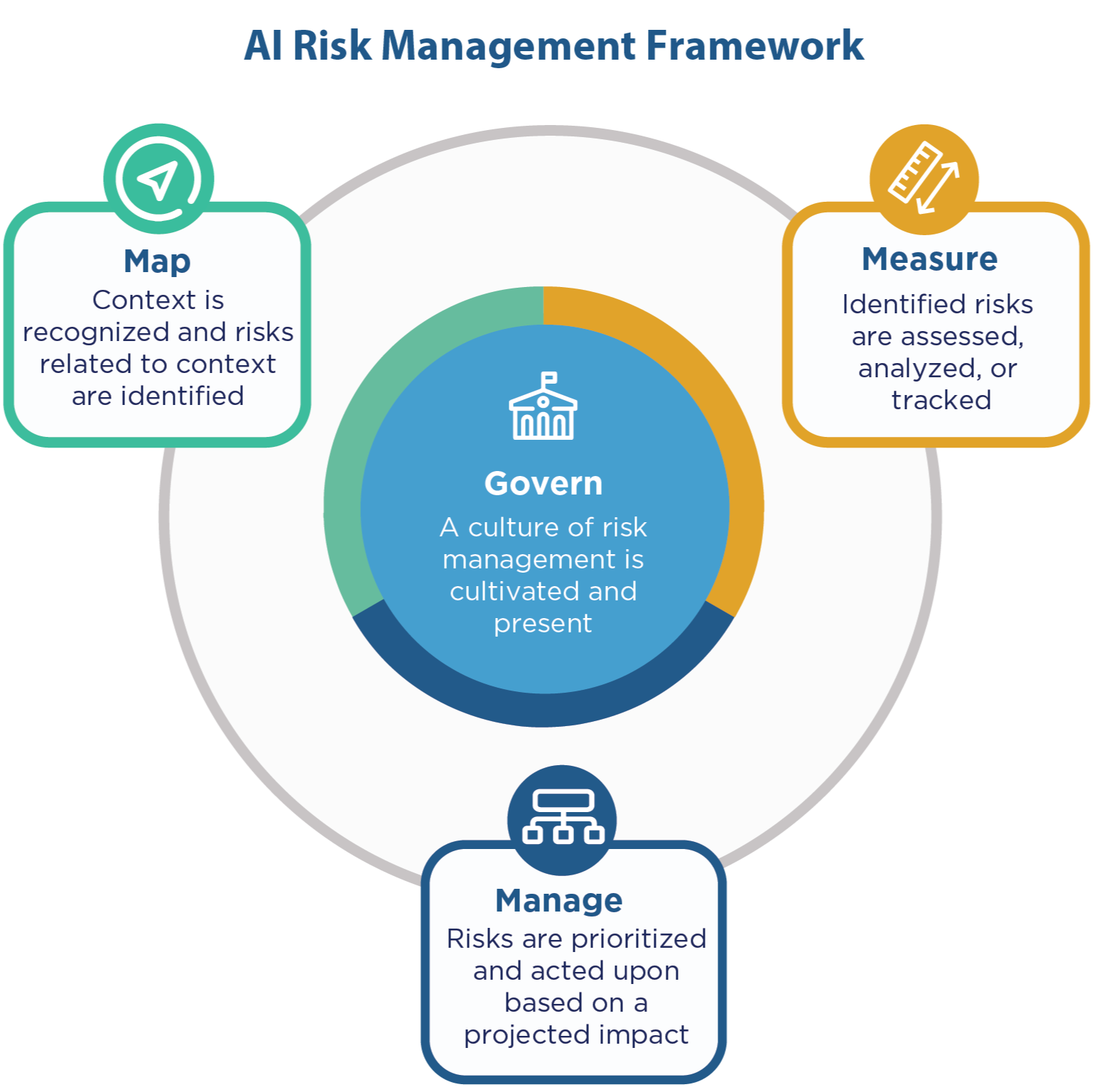
Part 2 of our series dives into the Measure and Manage functions of NIST’s AI RMF v1.0. We explore how to assess and mitigate AI risks in practice, offer implementation tips and tools, discuss the framework’s limitations, and provide a handy checklist to apply to your own AI projects.
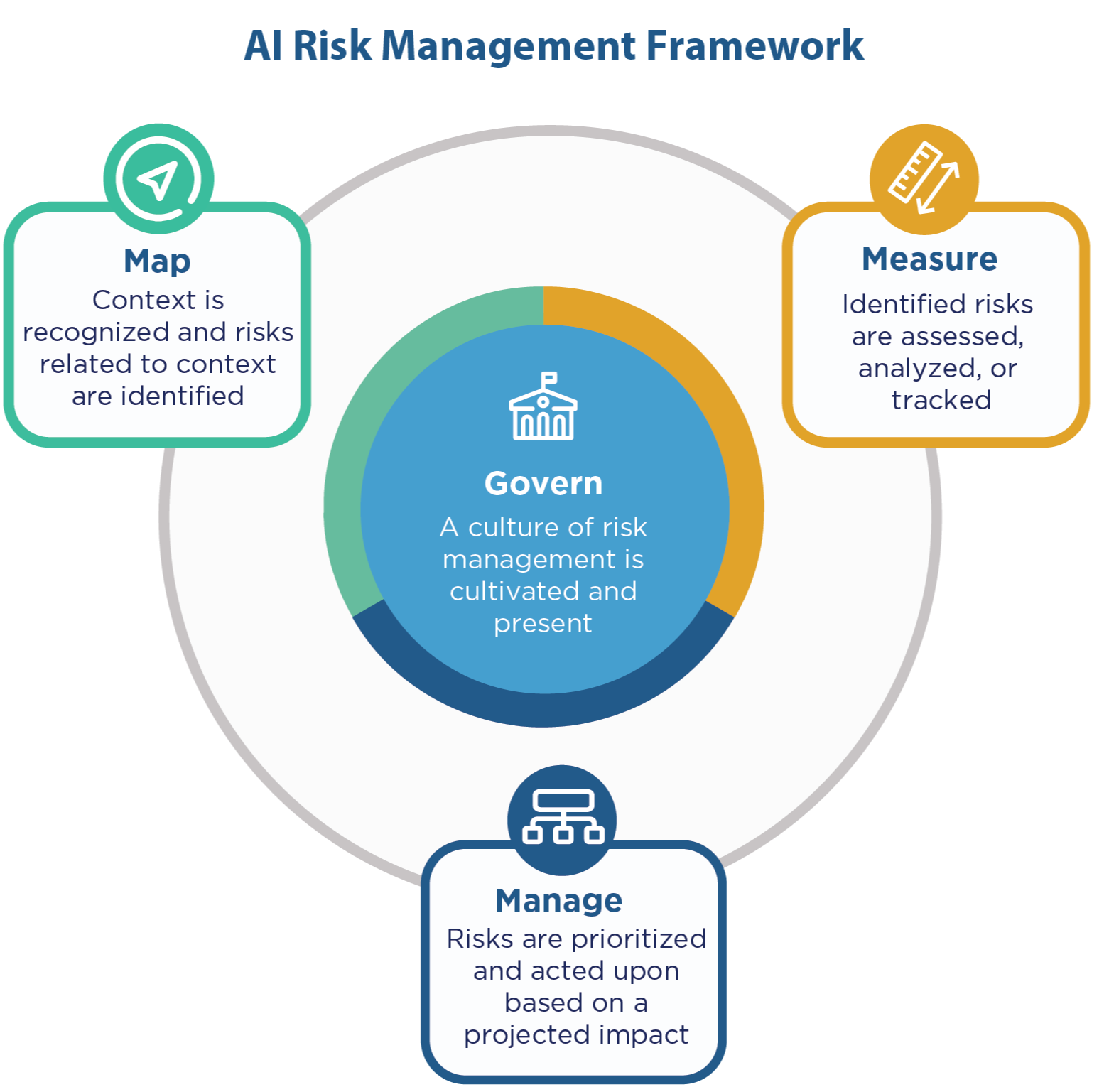
Why AI risk management matters, an overview of NIST’s AI RMF v1.0, and a breakdown of its first two core functions: Govern and Map.
Learn the fundamentals of penetration testing, essential tools, and methodologies that every aspiring ethical hacker should know.
A comprehensive guide to starting your journey in cybersecurity, covering essential tools, methodologies, and career paths.
Learn the basics of Open Source Intelligence gathering, tools, and techniques used by cybersecurity professionals.