Splunk Part 02: MITRE ATT&CK and Behavioral Mapping

Welcome Back!
In Part 01, Splunk Enterprise was installed and verified, and basic SPL searches were used to confirm indexing and search functionality. At this stage, Splunk is operational and capable of storing and querying event data. What has not yet been addressed is how that data is evaluated from a security and adversary-behavior perspective.
Splunk does not determine whether activity is malicious on its own. It indexes events and returns results based on search criteria. Determining whether those events represent an attack requires a behavioral framework. In modern security operations, that framework is commonly provided by MITRE ATT&CK.
This part introduces MITRE ATT&CK and explains how it is used to structure security analysis in Splunk environments before any detections or alerts are built.
What MITRE ATT&CK Is
MITRE ATT&CK is a behavior-based knowledge base documenting adversary tactics and techniques observed in real-world intrusions. It does not describe vulnerabilities, malware signatures, or defensive products. Instead, it focuses on what attackers do after gaining access to an environment.
ATT&CK is structured around three core elements:
- Tactics, which describe the adversary’s objective
- Techniques, which describe how that objective is achieved
- Sub-techniques, which provide additional behavioral detail
This structure allows defenders to analyze activity based on behavior rather than tooling. Because attackers routinely change tools, behavior-based analysis remains effective even when malware indicators become outdated.
Why MITRE ATT&CK Is Used in Security Operations
MITRE ATT&CK is widely adopted across SOCs, detection engineering teams, and threat-hunting programs because it provides a standardized language for adversary behavior.
Organizations use ATT&CK to:
- Design and validate detections
- Assess coverage across the attack lifecycle
- Perform structured threat hunting
- Communicate findings consistently between teams
ATT&CK does not replace a SIEM platform. It provides the analytical context needed to interpret SIEM data correctly.
How ATT&CK Relates to Splunk
Splunk and MITRE ATT&CK serve different roles.
Splunk is responsible for ingesting, indexing, and searching event data. MITRE ATT&CK provides a taxonomy for classifying adversary behavior. Splunk does not automatically apply ATT&CK techniques to events. Mapping occurs at the search and analytics layer, where analysts determine how patterns in log data correspond to documented techniques.
This separation is intentional. ATT&CK is platform-agnostic, and Splunk is data-source agnostic. The relationship between them is defined by analysis, not automation.
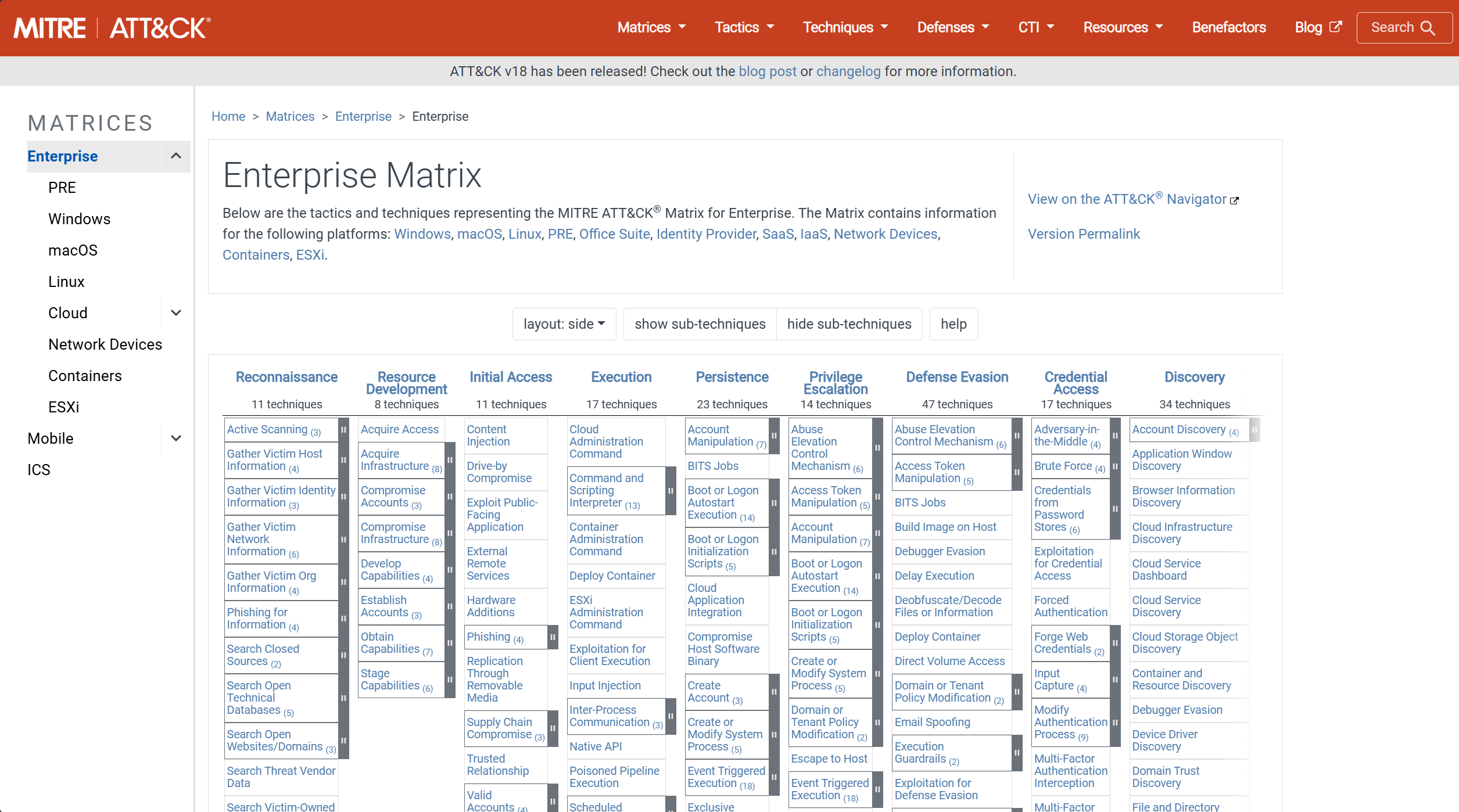
ATT&CK Tactics as an Analytical Structure
ATT&CK tactics represent stages or objectives within an attack. The Enterprise Matrix includes the following tactics:
- Reconnaissance
- Resource Development
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration
- Impact
Rather than searching logs without direction, analysts use these tactics to scope analysis. Each tactic implies a category of behavior that may be observable in logs. This structure helps reduce noise and ensures coverage across multiple phases of an intrusion.
Understanding Logs as Behavioral Evidence
ATT&CK techniques are not represented by single log entries. They are inferred from patterns of activity over time.
For example, a single process execution event may be benign. Repeated execution of scripting interpreters, unexpected parent-child process relationships, or abnormal execution timing may support execution-related techniques.
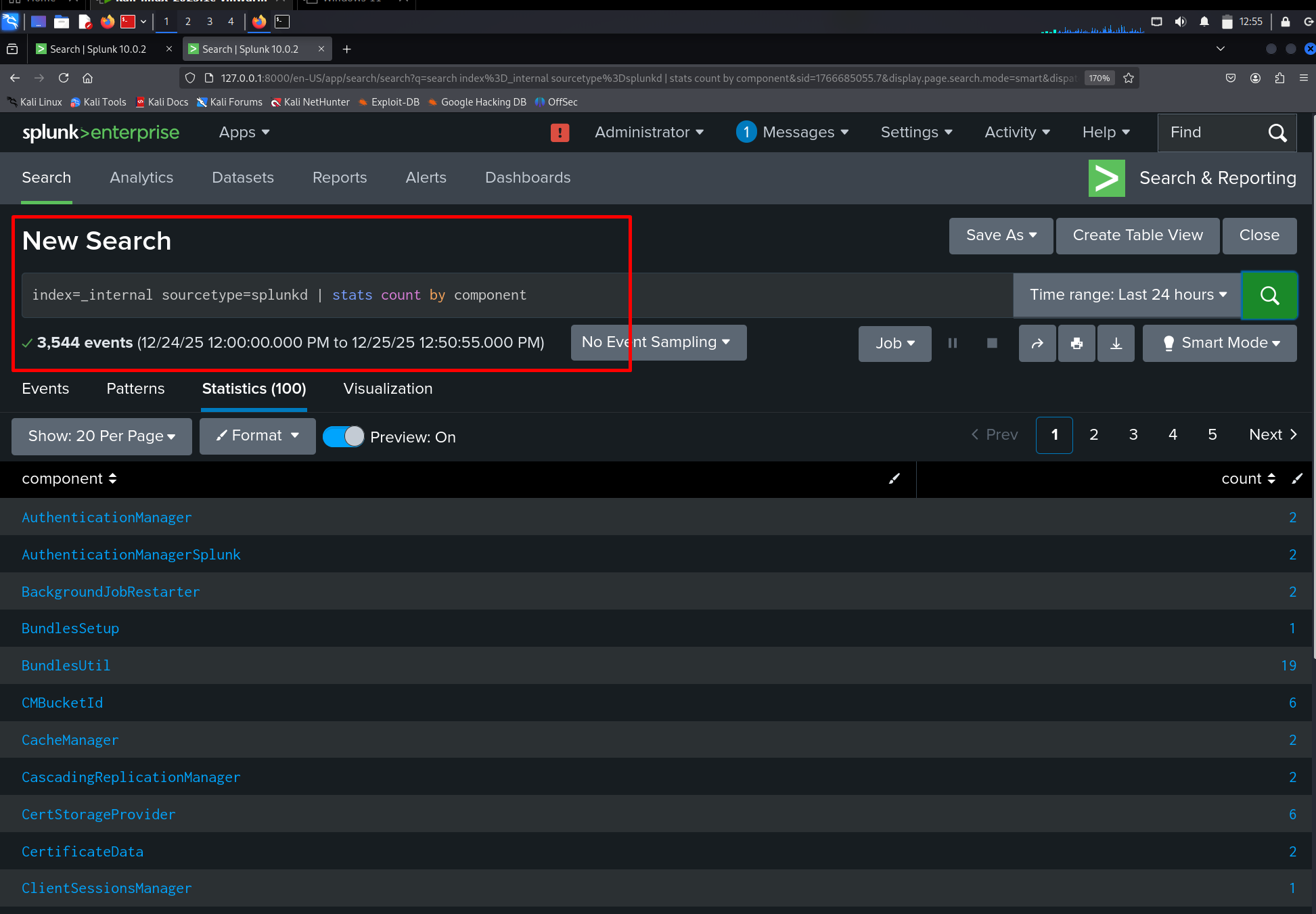
Splunk enables this type of analysis through aggregation and summarization using SPL. In Part 01, internal logs were used to demonstrate this capability:
index=_internal sourcetype=splunkd | stats count by componentWhile this query is not security-focused, it illustrates how activity can be summarized across dimensions. The same approach is later used to summarize authentication events, process creation, or network activity when analyzing ATT&CK techniques.
Scope of This Part
This part is intentionally limited in scope.
It does not include alert creation, detection logic, dashboards, or automation. The objective is to establish a behavioral and analytical foundation before detections are introduced.
Attempting to build alerts without understanding ATT&CK often results in detections that are noisy, incomplete, or poorly aligned with real adversary behavior.
Splunk is now positioned as an analysis platform rather than just a log repository. With a clear understanding of how MITRE ATT&CK models adversary behavior, security events can be evaluated in terms of tactics and techniques instead of isolated log entries.
In the next part, ATT&CK techniques will be translated into concrete SPL searches using security-relevant data sources, marking the transition from framework understanding to applied detection.
Stay Curious!